A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information.
“The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as ‘Viper,'” Cluster25 said in a report published last week.
“The target of this attack is currently unknown but with high probability, given the previous history of the attack perpetrated by the group, it might be a government institution from a South Asian country.”
Override Panda, also called Naikon, Hellsing, and Bronze Geneva, is known to operate on behalf of Chinese interests since at least 2005 to conduct intelligence-gathering operations targeting ASEAN countries.
Attack chains unleashed by the threat actor have involved the use of decoy documents attached to spear-phishing emails that are designed to entice the intended victims to open and compromise themselves with malware.
Last April, the group was linked to a wide-ranging cyberespionage campaign directed against military organizations in Southeast Asia. Then in August 2021, Naikon was implicated in cyberattacks targeting the telecom sector in the region in late 2020.
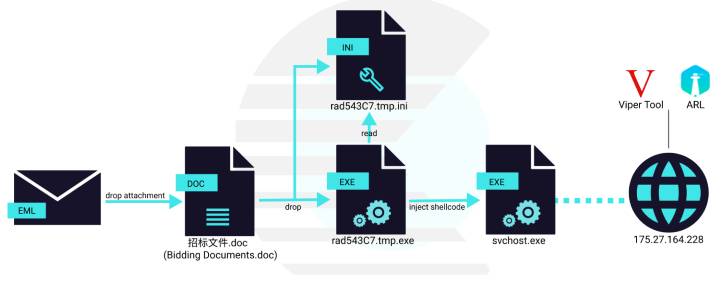
The latest campaign spotted by Cluster25 is no different in that it leverages a weaponized Microsoft Office document to kick-start the infection killchain that includes a loader designed to launch a shellcode, which, in turn, injects a beacon for the Viper red team tool.
Available for download from GitHub, Viper is described as a “graphical intranet penetration tool, which modularizes and weaponizes the tactics and technologies commonly used in the process of Intranet penetration.”
The framework, similar to Cobalt Strike, is said to feature over 80 modules to facilitate initial access, persistence, privilege escalation, credential Access, lateral movement, and arbitrary command execution.
“By observing Naikon APT’s hacking arsenal, it was concluded that this group tends to conduct long-term intelligence and espionage operations, typical for a group that aims to conduct attacks on foreign governments and officials,” the researchers pointed out.
“To avoid detection and maximize the result, it changed different [tactics, techniques, and procedures] and tools over time.”