Three high-impact security vulnerabilities have been disclosed in APC Smart-UPS devices that could be abused by remote adversaries as a physical weapon to access and control them in an unauthorized manner.
Collectively dubbed TLStorm, the flaws “allow for complete remote takeover of Smart-UPS devices and the ability to carry out extreme cyber-physical attacks,” Ben Seri and Barak Hadad, researchers from IoT security company Armis, said in a report published Tuesday.
Uninterruptible power supply (UPS) devices function as emergency backup power providers in mission-critical environments such as medical facilities, server rooms, and industrial systems. Most of the afflicted devices, totaling over 20 million, have been identified so far in healthcare, retail, industrial, and government sectors.
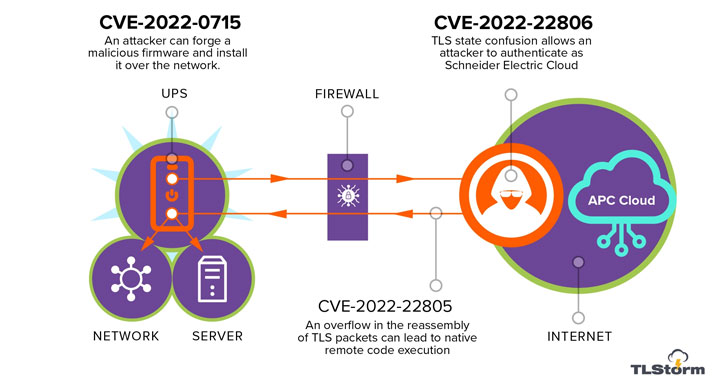
TLStorm consists of a trio of critical flaws that can be triggered via unauthenticated network packets without requiring any user interaction, meaning it’s a zero-click attack, with two of the issues involving a case of faulty TLS handshake between the UPS and the APC cloud –
- CVE-2022-22805 (CVSS score: 9.0) – TLS buffer overflow
- CVE-2022-22806 (CVSS score: 9.0) – TLS authentication bypass
- CVE-2022-0715 (CVSS score: 8.9) – Unsigned firmware upgrade that can be updated over the network
Successful exploitation of any of the flaws could result in remote code execution (RCE) attacks on vulnerable devices, which in turn could be weaponized to tamper with the operations of the UPS to physically damage the device or other assets connected to it.
“By using our RCE vulnerability we were able to bypass the software protection and let the current spike periods run over and over until the DC link capacitor heated up to ~150 degrees celsius (~300F), which caused the capacitor to burst and brick the UPS in a cloud of electrolyte gas, causing collateral damage to the device,” the researchers explained.
To make matters worse, the flaw in the firmware upgrade mechanism could be leveraged to plant a malicious update on UPS devices, enabling the attackers to establish persistence for extended periods of time and use the compromised host as a gateway for further attacks.
“Abusing flaws in firmware upgrade mechanisms is becoming a standard practice of APTs, as has been recently detailed in the analysis of the Cyclops Blink malware, and improper signing of firmwares of embedded devices is a recurring flaw in various embedded systems,” the researchers said.
Following responsible disclosure to Schneider Electric on October 31, 2021, fixes have been released as part of Patch Tuesday updates on March 8, 2022. Customers are recommended to install the updates provided to reduce the risk of successful exploitation of these vulnerabilities.
“UPS devices, like many other digital infrastructure appliances, are often installed and forgotten,” the researchers concluded. “Since these devices are connected to the same internal networks as the core business systems, exploitation attempts can have severe implications.”