Cybersecurity researchers have disclosed an unpatched flaw in Apple Pay that attackers could abuse to make an unauthorized Visa payment with a locked iPhone by taking advantage of the Express Travel mode set up in the device’s wallet.
“An attacker only needs a stolen, powered on iPhone. The transactions could also be relayed from an iPhone inside someone’s bag, without their knowledge,” a group of academics from the University of Birmingham and University of Surrey said. “The attacker needs no assistance from the merchant and backend fraud detection checks have not stopped any of our test payments.”
Express Travel is a feature that allows users of iPhone and Apple Watch to make quick contactless payments for public transit without having to wake or unlock the device, open an app, or even validate with Face ID, Touch ID or a passcode.
The man-in-the-middle (MitM) replay and relay attack, which involves bypassing the lock screen to make a payment to any EMV reader illicitly, is made possible due to a combination of flaws in both Apple Pay and Visa’s system, and doesn’t impact, say, Mastercard on Apple Pay or Visa cards on Samsung Pay.
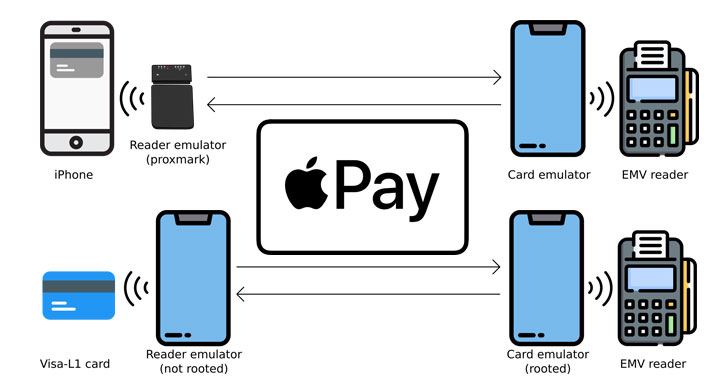
The modus operandi hinges on mimicking a transit gate transaction by using a Proxmark device that acts as an EMV card reader communicating with a victim’s iPhone and an NFC-enabled Android app that functions as a card emulator to relay signals to a payment terminal.
Specifically, it takes advantage of a unique code — aka Magic Bytes — broadcast by the transit gates to unlock Apple Pay, resulting in a scenario whereby replaying the sequence of bytes, the Apple device is deceived into authorizing a rogue transaction as if it’s originated from the ticket barrier, when, in reality, it’s been triggered via a contactless payment terminal under the attacker’s control.
At the same time, the EMV reader is also tricked into believing that on-device user authentication has been performed, thus enabling payments of any amount to be made without the iPhone user’s knowledge.
Apple and Visa were alerted to the vulnerability in October 2020 and May 2021, respectively, the researchers said, adding, “both parties acknowledge the seriousness of the vulnerability, but have not come to an agreement on which party should implement a fix.”
In a statement shared with the BBC, Visa said this type of attack was “impractical,” adding, “Variations of contactless fraud schemes have been studied in laboratory settings for more than a decade and have proven to be impractical to execute at scale in the real world.”
“This is a concern with a Visa system but Visa does not believe this kind of fraud is likely to take place in the real world given the multiple layers of security in place,” an Apple spokesperson was quoted as saying to the U.K. national broadcaster.