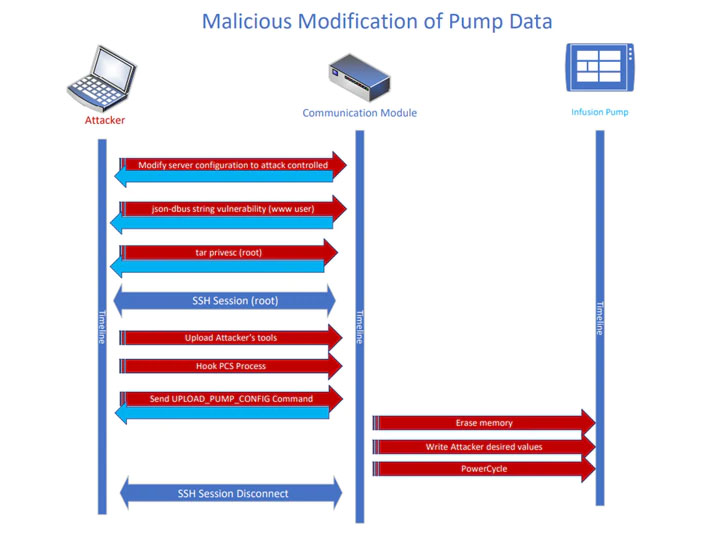
Cybersecurity researchers have disclosed five previously unreported security vulnerabilities affecting B. Braun’s Infusomat Space Large Volume Pump and SpaceStation that could be abused by malicious parties to tamper with medication doses without any prior authentication.
McAfee, which discovered and reported the flaws to the German medical and pharmaceutical device company on January 11, 2021, said the “modification could appear as a device malfunction and be noticed only after a substantial amount of drug has been dispensed to a patient, since the infusion pump displays exactly what was prescribed, all while dispensing potentially lethal doses of medication.”
The issues have been addressed by B. Braun in SpaceCom L82 or later, Battery Pack SP with WiFi:L82 or later, and DataModule compactplus version A12 or later.
Infusion pumps are medical devices used to deliver intravenous fluids, such as nutrients and medications, into a patient’s body in controlled amounts, while SpaceStation is a configurable docking and communication system designed to accommodate up to four infusion pumps for use in a medical facility. The devices run on a software component called SpaceCom, an embedded Linux system that runs either on the pump from within its smart battery pack or from inside the SpaceStation.
In a nutshell, the flaws identified by McAfee enables an attacker to escalate privileges, view sensitive information, upload arbitrary files, and perform remote code execution —
- CVE-2021-33885 – Insufficient Verification of Data Authenticity (CVSS 9.7)
- CVE-2021-33882 – Missing Authentication for Critical Function (CVSS 8.2)
- CVE-2021-33886 – Use of Externally-Controlled Format String (CVSS 7.7)
- CVE-2021-33883 – Cleartext Transmission of Sensitive Information (CVSS 7.1)
- CVE-2021-33884 – Unrestricted Upload of File with Dangerous Type (CVSS 5.8)
By chaining together the vulnerabilities, an adversary could “modify a pump’s configuration while the pump is in standby mode, resulting in an unexpected dose of medication being delivered to a patient on its next use – all with zero authentication,” McAfee Advanced Threat Research team noted in a technical deep-dive.
Put differently, the weaknesses, which arise due to a lack of verification in the pump’s operating system, could allow any attacker to send commands or data to it, thereby facilitating remote attacks that not only go undetected but also weaponize the device by altering the amount of medication a patient is expected to receive through infusion.
One caveat of note is that the attacks can only be successful when a pump is idle or in standby mode in between infusions, not to mention such unauthorized modifications to critical pump data necessitate that the threat actor first gain an initial foothold to the local network, or potentially carry out the intrusions over the internet in the event the pumps are directly exposed — a scenario that’s unlikely.
“All facilities utilizing SpaceCom, Battery Pack SP with WiFi, and DataModule compactplus should review their IT infrastructure to ensure that a network zone concept has been implemented whereby critical systems, such as infusion pumps, are housed in separate (e.g., by firewalls or VLAN) environments which are not accessible directly from the internet or by unauthorized users,” B. Braun said in an advisory published on May 14, 2021.
“Wireless networks should be implemented using multi-factor authentication and industry standard encryption and should be equipped with Intrusion Detection Systems (IDS) and/or Intrusion Prevention Systems (IPS),” the company added.