Law enforcement authorities in the Netherlands have arrested two alleged individuals belonging to a Dutch cybercriminal collective who were involved in developing, selling, and renting sophisticated phishing frameworks to other threat actors in what’s known as a “Fraud-as-a-Service” operation.
The apprehended suspects, a 24-year-old software engineer, and a 15-year-old boy, are said to have been the main developer and seller of the phishing frameworks that were employed to collect login data from bank customers. The attacks primarily singled out users in the Netherlands and Belgium.
“The phishing frameworks allow attackers with minimal skills to optimize the creation and design of phishing campaigns to carry out massive fraudulent operations all the while bypassing 2FA,” Group-IB Europe’s Roberto Martinez, senior threat intelligence analyst, and Anton Ushakov, deputy head of the high-tech crime investigation department, in a report, adding the gang “advertises their services and interacts with fellow cybercriminals on Telegram messenger.”
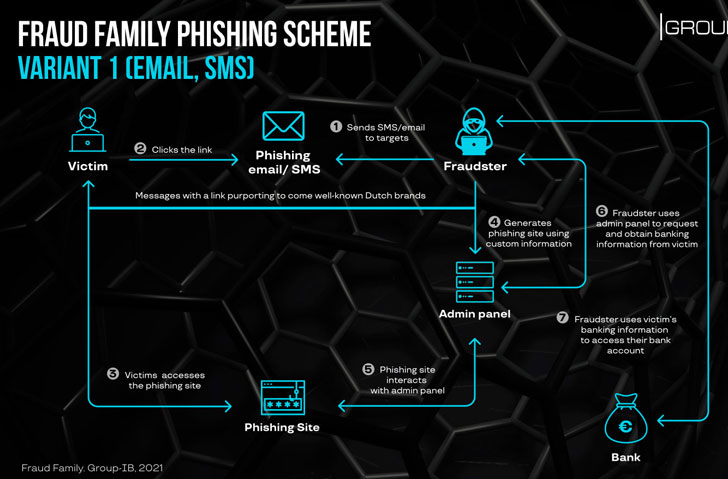
Infections involving Fraud Family commences with an email, SMS, or WhatsApp message impersonating well-known local brands containing malicious links that, when clicked, redirect the unsuspecting recipient to adversary-controlled payment info-stealing phishing websites. In an alternative attack scenario, the fraudsters were observed posing as a buyer on a Dutch classified advertising platform to contact a seller and subsequently move the conversation to WhatsApp to trick the latter into visiting a phishing site.
Group-IB researchers noted the “high level of personalization” offered by the phishing websites, which not only impersonate a legitimate Dutch marketplace, but also claims to use a well-known e-commerce payment system in the country, only to lead the victim to a fake bank webpage from where the credentials are siphoned based on the bank selected.
“When victims submit their banking credentials, the phishing site sends them to the fraudster-controlled web panel,” Group-IB said. “This one actually notifies the miscreants that a new victim is online. The scammers can then request additional information that will help them to gain access to the bank accounts, including two factor authentication tokens, and personal identifiable information.”
According to messages posted by the group on Telegram, the web panels — one of which is a fork of another panel called “U-Admin” — can be rented for €200 a month (Express Panel), or for €250 should other cybercriminals opt for the Reliable Panel (or Reliable Admin). No fewer than eight Telegram channels operated by Fraud Family have been identified to date, with the channels boasting 2,000 subscribers between them.
“The attacks that rely on Fraud Family’s infrastructure increased toward the final months of 2020,” Group-IB researchers said. “This trend continues in 2021 with the appearance of Express Panel and Reliable Panel.”