Cybersecurity researchers have disclosed new security vulnerabilities in the Etherpad text editor (version 1.8.13) that could potentially enable attackers to hijack administrator accounts, execute system commands, and even steal sensitive documents.
The two flaws — tracked as CVE-2021-34816 and CVE-2021-34817 — were discovered and reported on June 4 by researchers from SonarSource, following which patches have been shipped for the latter in version 1.8.14 of Etherpad released on July 4.
Etherpad is a real-time collaborative interface that enables a document to be edited simultaneously by multiple authors. It is an open-source alternative to Google Docs that can be hosted on your own servers.
“The XSS vulnerability allows attackers to take over Etherpad users, including admins. This can be used to steal or manipulate sensitive data,” SonarSource vulnerability researcher Paul Gerste said in a report shared with The Hacker News.
“The argument injection vulnerability allows attackers to execute arbitrary code on the server, which would allow [them] to steal, modify or delete all data, or to target other internal systems that are reachable from the server.”
Specifically, the XSS vulnerability (CVE-2021-34817) resides in the chat feature offered by Etherpad, with the “userId” property of a chat message — i.e., a unique identifier associated with a document author — rendered on the front-end without properly escaping special characters, thus permitting an adversary to insert a malicious JavaScript payload into the chat history and perform actions as a victim user.
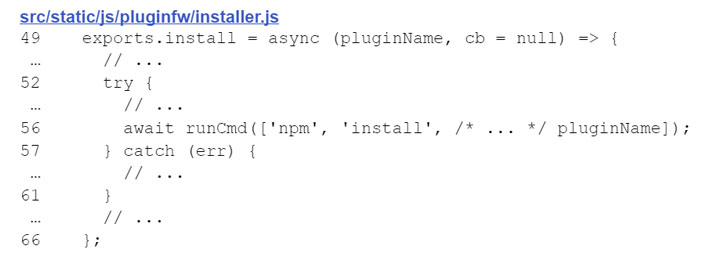
CVE-2021-34816, on the other hand, relates to how Etherpad manages plugins, wherein the name of the package to be installed via the “npm install” command is not adequately sanitized, leading to a scenario that could allow an attacker to “specify a malicious package from the NPM repository or to simply use a URL that points to a package on the attacker’s server.”
The consequence of successful exploitation of CVE-2021-34816 is the execution of arbitrary code and system commands, thus completely compromising the Etherpad instance and its data.
Concerningly, both vulnerabilities can be chained together by an attacker first to take over an administrator account and then use those privileges to gain a shell and execute malicious code on the server.
“Fixed a persistent XSS vulnerability in the Chat component,” Etherpad maintainers said in the release notes for version 1.8.14. “In case you can’t update to 1.8.14 directly, we strongly recommend to cherry-pick [commit] a796811.” It’s worth pointing out that the argument injection vulnerability remains unpatched, although the researchers note that the flaw is “significantly harder to exploit on its own.”
The research highlights “how important data validation and sanitization is for avoiding such flaws during development,” Gerste said, adding, “the smallest coding mistake can be the first stepping stone for an attacker to launch further attacks against the software.”
Etherpad users are highly advised to update their installations to version 1.8.14 to mitigate the risk associated with the flaw.